I read a chilling editorial over at SQL Server Central in regards to the growing threat of Ransomware.
Steve Jones presents a nightmare scenario for a business.
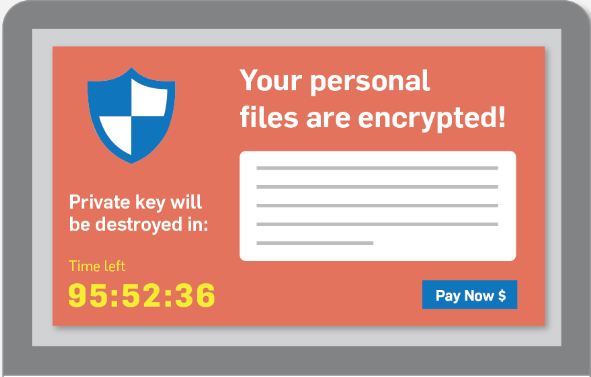
Imagine you come into work and all of your database columns are encrypted. You have no idea what key was used, and your application can’t access the data. You receive a message that for a $100,000 payment, the decryption key will be sent to you. What do you do?
There was a similar case at a Hollywood Presbyterian hospital which resulted in them going back to using paper and offloading cases to surrounding facilities until they paid the ransom. Apparently the FBI investigates these situations and recommends to businesses to just pay the ransom.
With ransomware attacks expected to grow it is more imperative than ever to have a good disaster recovery plan in place. Not only do you need to have these plans in place, but they need to be periodically tested so the business can understand how long it would take to be back up from a disaster.
I appreciate the approach Brent Ozar’s crew takes when first looking into DR / HA for a business. They have planning worksheets that break down the Recovery Time Objectives and associated cost ranges. If you are new to DR / HA this is a good read. They also have a video on the topic.
Have you heard of any instances of ransomware anywhere you have been, and did they change the focus on the disaster recovery plans?
Let’s discuss in the comments below.


The post have resolved our problem,thanks very much and hope you writting more good articles.